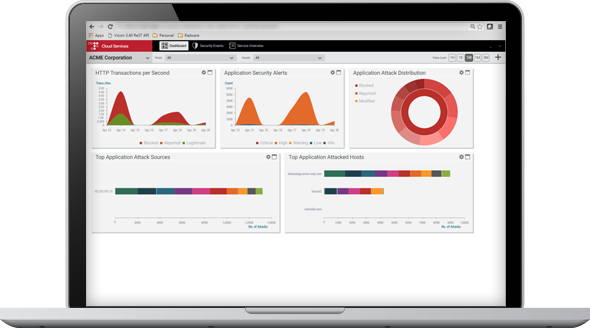
Business Driver: Radware Cloud Web Application Firewall – WAF
As our Cloud computing dependence grows so too does our reliance upon “always-on” Software as a Service” (SaaS) offerings from vendors. Protecting the interface between user and application within the Cloud poses risks for organisations with sensitive data or a critical reliance upon SaaS service providers, particularly e-commerce. Protecting revenue streams and service availability is a vital piece of a robust business continuity plan. For demanding environments where outages are measured in thousands of dollars per minute, implementing WAF systems is a high-value mitigation investment.
Radware Cloud: WAF Product Overview
Web applications have become more complex and sophisticated through necessity. Users demand new features and management expect a proportional increase in employee productivity. Downtime and system outages are intolerable because of reputational damage or revenue losses. Radware’s Cloud products provide comprehensive mitigation measure that protect organisations from Web bound threats.