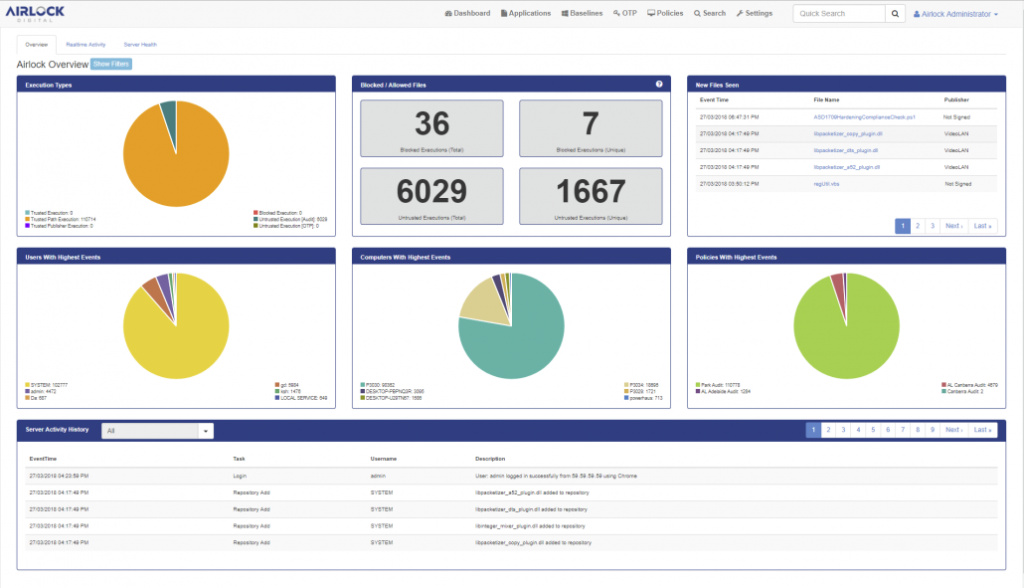
Business Driver: Airlock Digital Whitelisting
In spite of years of adversarial security challenges, Cybersecurity is still in a constant state of flux. Ransomware and a multitude of malicious attack vectors keep organisations constantly on their toes, trying to locate that magic security bullet that many vendor’s claim their product fulfills. The reality is that information security is at its most effective when a layered approach is applied that address risks with the most effective products or solutions. Application Whitelisting is one such approach that prevents malicious code executing without pre-approval. Put simply, white-listing prevents bad software from operating unless the organisation’s IT administrator’s give it the all-clear.